-
-
Notifications
You must be signed in to change notification settings - Fork 5.4k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Add Gitea secrets storage and management #14483
Conversation
|
Does this close #12065? |
|
Yes, this could be used to resolve that |
|
Any update on this? |
1 similar comment
|
Any update on this? |
|
@lafriks Could I pick up this PR? |
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: delvh <dev.lh@web.de>
Co-authored-by: delvh <dev.lh@web.de>
services/secrets/secrets.go
Outdated
| }) | ||
| } | ||
|
|
||
| func InsertOrgSecret(ctx context.Context, userID int64, key, data string) error { |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
There is a name mismatch here: InsertOrgSecret and FindUserSecrets. I would rename both to Owner. Maybe change the structs member too.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I agree about the struct fields.
But we should find a name to stick with as OwnerSecret sounds abolutely wrong to me and doesn't clarify the difference to RepoSecrets enough.
What about UserSecrets instead, even if they can also be for an organization?
|
This PR has currently secrets on Repo and Organisation level. Could you also add Secrets to the User level, that would apply to all personal Projects? |
|
I have thought about that as well, but what would the benefit be? |
|
The same as org secrets? Available for every repo. The package registry may need secrets at the owner (user/org) level too. The Debian registry for example uses a gpg key to sign data which could be stored in the secrets. |
|
Okay, yes that's makes sense. |
I need them. On GitLab I have a lot of personal projects. Mostly little tools. Almost all have a CI (mostly just publish to e.g.g PyPI on a new Release). a lot of them share the same secrets (e.g. PyPI credentials). As GitLab does not allow secrets on User level, I need to add everything for each Repo new and when something changed, that means a lot of work for me, to change it for every single Repo. I'm currently moving to Codebreg, which uses Gitea. If you add add secrets management, it would be great to allow this on User level to save me a lot of Work. Of course, I could create a Org just for my personal projects, but that feels a little bit unnecessary. |
services/secrets/secrets.go
Outdated
| }) | ||
| } | ||
|
|
||
| func InsertOrgSecret(ctx context.Context, userID int64, key, data string) error { |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I agree about the struct fields.
But we should find a name to stick with as OwnerSecret sounds abolutely wrong to me and doesn't clarify the difference to RepoSecrets enough.
What about UserSecrets instead, even if they can also be for an organization?
| @@ -1,6 +1,5 @@ | |||
| // Copyright 2021 The Gitea Authors. All rights reserved. | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Do we copyright the year the code was written, or the year it is merged?
I would have thought it is the year it is merged…
models/auth/secret.go
Outdated
| UserID int64 `xorm:"index NOTNULL"` | ||
| RepoID int64 `xorm:"index NOTNULL"` | ||
| Name string `xorm:"NOTNULL"` |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Could it be that the suggestions in this file were missed?
| } | ||
|
|
||
| func InsertRepoSecret(ctx context.Context, repoID int64, key, data string) error { | ||
| v, err := EncryptString(data) |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think I've also mentioned it above, but here it is again:
I think it would be a good idea to strip leading and trailing whitespace from secrets.
There is only a marginal benefit in not doing it (who has a secret that starts or ends with whitespace?).
However, there is a huge benefit for usability, since many copying programs add for example whitespace at the end, meaning you would get an invalid secret that you first have to debug why it isn't working.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Solved in the new PR.
| settings.pull_request_read_hint = Allow pull request read the secret | ||
| settings.add_secret = Add Secret | ||
| settings.add_secret_success = The secret '%s' has been added. | ||
| settings.secret_value_content_placeholder = Input any content |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Assuming my suggestion above is implemented:
| settings.secret_value_content_placeholder = Input any content | |
| settings.secret_value_content_placeholder = Input any content. Whitespace at the start and end will be omitted. |
Then suddenly this placeholder isn't redundant anymore.
|
Hi guys, I wonder if I can start a new PR with all commits kept? I tried to fix problems ASAP to stop blocking #21937, and @lafriks kindly gave me access to push to his branch, but I still can't mark comments resolved or update the PR content to explain what I'm trying to do, because I'm not the poster. I think it's OK yet, but if we want to add more to this PR like "secrets for users" or "trimming whitespace", I think I can handle it faster with a new PR. I know it will cause some inconvenience to reviewers, so I think it's also a good idea to merge this PR with some todos left, and start a new PR to finish them. What do you think? |
I personally prefer to leave some todo like supporting user level secrets in next PRs and we can merge this one ASAP. |
|
In the process of helping to fix problems, I took a close look at the code. Finally, to be honest, I am against this PR. The point is that I think we don't need a new MasterKey, we should use SecretKey. These are my reasons:
If we agree to give up MasterKey, some commits and comments will be out of topic. So I will start a new PR as an alternative with necessary commits kept, and if I'm wrong, we can continue with this one. See: |
| @@ -51,6 +52,10 @@ func DeleteRepository(ctx context.Context, doer *user_model.User, repo *repo_mod | |||
| return err | |||
| } | |||
|
|
|||
| if err := secret_service.DeleteSecretsByRepoID(ctx, repo.ID); err != nil { | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I thought you would simply use models.DeleteRepository#130-152 for it…
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Solved in the new PR.
| @@ -39,6 +40,10 @@ func DeleteOrganization(org *organization.Organization) error { | |||
| return models.ErrUserOwnPackages{UID: org.ID} | |||
| } | |||
|
|
|||
| if err := secret_service.DeleteSecretsByOwnerID(ctx, org.ID); err != nil { | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I thought you would simply use models/DeleteUser#72-91.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Solved in the new PR.
| OwnerID int64 `xorm:"UNIQUE(owner_repo_name) NOTNULL"` | ||
| RepoID int64 `xorm:"UNIQUE(owner_repo_name) NOTNULL"` |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I think we should not remove the indexes. They can still be valuable.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Solved in the new PR.
|
I think we can close this and switch to #22142 |
Fork of #14483, but [gave up MasterKey](#14483 (comment)), and fixed some problems. Close #12065. Needed by #13539. Featrues: - Secrets for repo and org, not user yet. - Use SecretKey to encrypte/encrypt secrets. - Trim spaces of secret value. - Add a new locale ini block, to make it easy to support secrets for user. Snapshots: Repo level secrets: 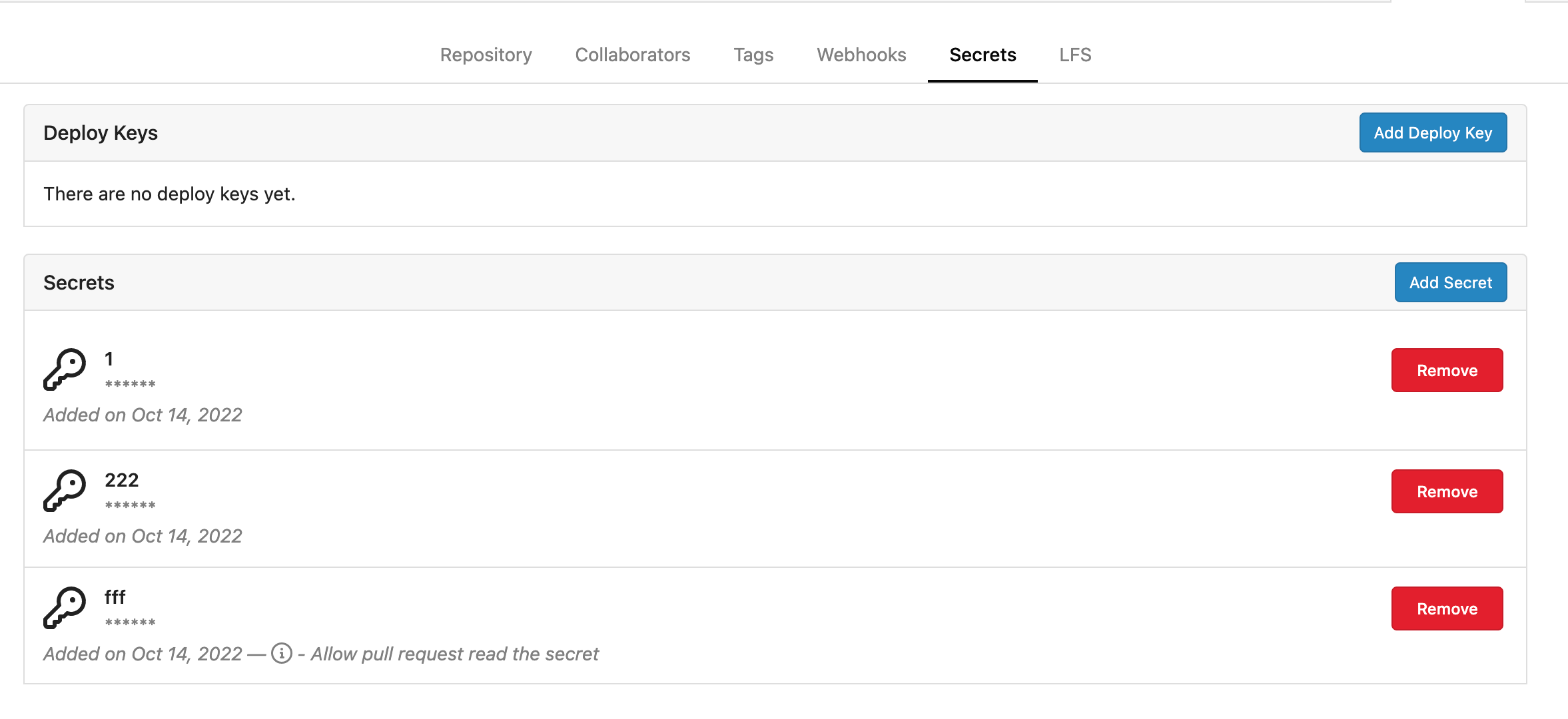 Rrg level secrets 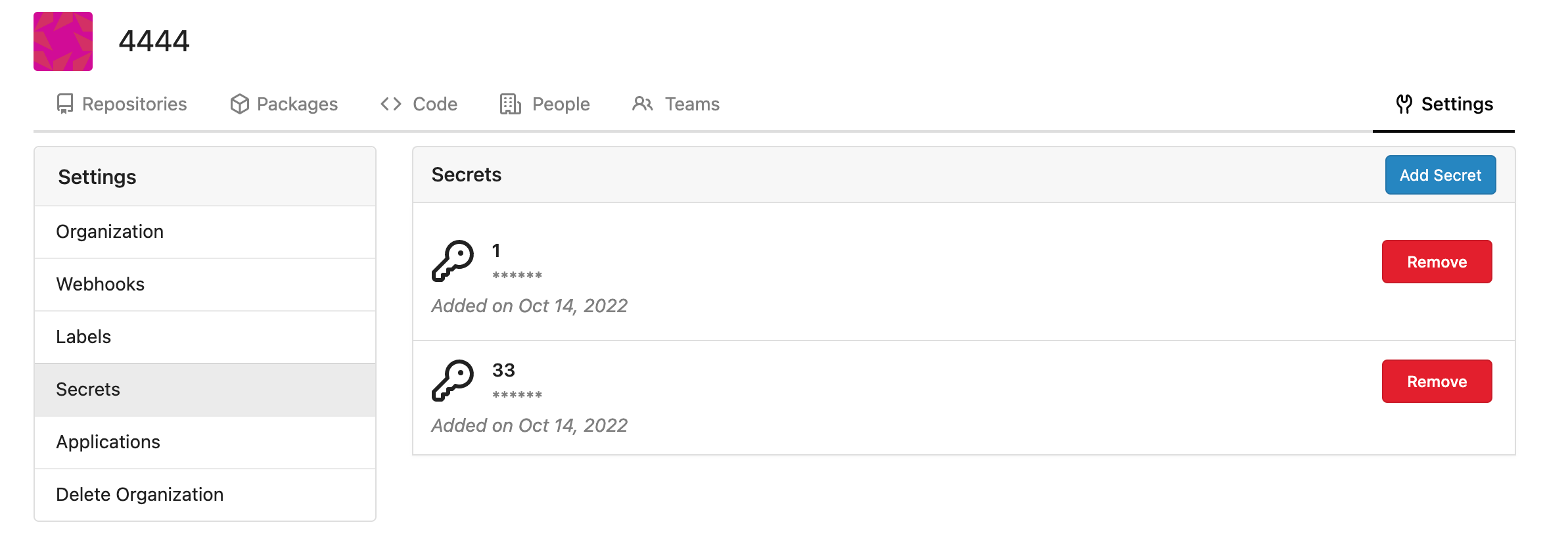 Co-authored-by: Lauris BH <lauris@nix.lv> Co-authored-by: Lunny Xiao <xiaolunwen@gmail.com> Co-authored-by: wxiaoguang <wxiaoguang@gmail.com> Co-authored-by: delvh <dev.lh@web.de> Co-authored-by: KN4CK3R <admin@oldschoolhack.me>
|
replaced by #22142 |
Also needed for #13539
some screenshots:

repository level secrets
org level secrets
