Releases: ZiggyCreatures/FusionCache
v1.4.0
Important
Although when updating to a new version it's the norm to update all referenced packages at once, this time is even more important. Because of a small change in the IFusionCacheSerializer interface, it is highly suggested to update all packages, including in transitive dependencies.
🚀 Add support for RecyclableMemoryStream to serializers (docs)
It is now possible to use RecyclableMemoryStreams with some of the supported serializers.
It's opt-in, meaning totally optional, and it's possible to use the default configuration or to specify one in the constructor, for maximum control and to fine-tune it however we want.
Thanks @viniciusvarzea for the suggestion!
See here for the original issue.
🔭 Better observability for GET operations (docs)
Community user @dotTrench noticed that when using OpenTelemetry, GET activities (TryGet, GetOrDefault, etc) were not including a useful bit of information: the hit/miss status.
While adding support for it via an extra tag, it was also noticed that it was not including another useful bit of information: the stale/fresh status.
Now this is solved, thanks to 2 new tags.
See here for the original issue.
💣 Throw specific exception when factory fails without fail-safe (docs)
Since v1.3.0 it's possible to trigger a factory fail without throwing an exception, so that fail-safe can kick in and do its thing.
But what happens if fail-safe is not enabled or if there's no stale value to fall back to?
Previously a plain Exception was being thrown, but that is hardly a best practice: now a more specific exception type has been created and will be thrown instead, namely FusionCacheFactoryException.
See here for the original issue.
🛑 Add cancellation support to serializers (docs)
Previously serializers did not support cancellation: now this is supported, via the standard CancellationTokens.
Thanks @b-c-lucas for noticing it!
See here for the original issue.
🚀 Better perf for FusionCacheProvider (docs)
Community user @MarkCiliaVincenti contributed with a PR that improved the performance of FusionCacheProvider, used with Named Caches, thanks to the use of FrozenDictionary.
See here for the original PR.
🐞 Respect the Size of an entry loaded in L1 from L2 (docs)
Community user @Amberg noticed that when the MemoryCache (L1) passed to FusionCache had a SizeLimit configured, and an entry wasbeing saved with a Size specified, that was not used when automatically getting the same entry from another node via the distributed cache, causing an issue.
Now this is solved, in 2 different scenarios:
- common case: setting an entry WITH a specific size on a cache WITH size limit, and then getting the same entry from another cache (WITH size limit, too), meaning it restores the entry with its size
- edge case (and probably a wrong setup anyway): setting an entry WITHOUT a specific size on a cache WITHOUT a size limit, and then getting the same entry from another cache (but WITH size limit) works if there's at least a Size specified in the entry options (either for the specific method call or in the DefaultEntryOptions). This is more of an edge case, since usually what is logically the same cache should be configured the same for every instance (a.k.a. on every node)
See here for the original issue.
✅ Way better tests
As always some tests have been added for each new feature.
On top of that though, the testes have been changed to make them even more resilient to microscopic differences between different runtimes, OSs, etc: most of the problems were related to this almost unknown behaviour.
This helped make the entire test suite even more stable and with a predictable outcome, both locally and on GitHub actions.
Overall, FusionCache currently has around 750 tests, including combinatorial params.
See here for some juicy details.
📕 Docs
Updated some docs with the latest new things.
v1.3.0
♊ Auto-Clone (docs)
In general is never a good idea to mutate data retrieved from the cache: it should always be considered immutable/readonly.
To see why, read more in the docs.
Not all the scenarios where mutating a piece of data we got from the cache are necessarily wrong though, as users may have a particular use case where that may be needed, and ideally they should be abe to do that in an easy (and optimized!) way, by following the tried and true "it just works" mindset.
With Auto-Clone this is now possible.
A couple of details:
- it just works, out of the box
- is easy to use
- doesn't require extra coding/setup (it's just a new
EnableAutoCloneoption) - uses existing code infrastructure (eg: IFusionCacheSerializer)
- has granular control on a per-entry basis
- is performant (as much as possible)
Thanks to community users @JarrodOsborne and @kzkzg !
See here for the original issue.
💣 Fail-Safe Without Exceptions (docs)
Currently the way to activate fail-safe is for a factory to throw an exception.
This makes sense, since the whole point of fail-safe is to protect us when an error occurs while executing a factory.
But there may be other ways to do it, for example by using a variation of the Result Pattern or similar approaches, in which throwing an exception is not necessary.
This is now possible thanks to the new Fail(...) method on the FusionCacheFactoryExecutionContext<TValue> type, which we can access when executing a factory.
A quick example:
var productResult = await cache.GetOrSetAsync<Result<Product>>(
$"product:{id}",
async (ctx, ct) =>
{
var productResult = GetProductFromDb(id);
if (productResult.IsSuccess == false)
{
return ctx.Fail(productResult.Error);
}
return productResult;
},
opt => opt.SetDuration(duration).SetFailSafe(true)
);Thanks to community user @chrisbbe that noticed it!
See here for the original issue.
🧙♂️ Adaptive Caching on errors (docs)
Previously it was not possible to use adaptive caching when an error occurred during a factory execution.
This was usually not a big issue, but it left a particular edge case not fully uported: selectively enabling/disabling fail-safe on errors.
Now this is possible, in the usual unified way.
Thanks to community user @cmeyertons for spotting it, and for creating the PR that solved it.
See here for the original issue.
📦 More granular (and less) dependencies with multi-targeting
Thanks to a note by community user @thompson-tomo FusionCache now multi-targets different .NET vesions.
This was not needed per-se, but by doing it FusionCache can now have less dependencies for some TFMs.
See here for the original issue.
🚀 Better perf for FusionCacheProvider (docs)
Community user @0xced contributed with a PR that improved the performance of FusionCacheProvider, used with Named Caches.
See here for the original PR.
⚠️ Update dependencies for CVE-2024-30105
Communicty user @dependabot (😅) noticed CVE-2024-30105 and promptly bumped the referenced version of the System.Text.Json package.
Note that this is only related to the package ZiggyCreatures.FusionCache.Serialization.SystemTextJson.
✅ Better tests
Some tests have been added for each new feature, and overall better snapshot tests.
📕 Docs
Updated some docs with the latest new things.
v1.2.0
🔑 Added DI Keyed Services support (docs)
Since .NET 8 we now have native support for multiple services of the same type, identified by different names, thanks to the addition of so called keyed services.
The idea is basically that we can now register services not only by type but also by specifying the name, like this:
services.AddKeyedSingleton<MyService>("foo");
services.AddKeyedSingleton<MyService>("bar");and later is possible to resolve it by both the type and a name.
Another way is to simply mark a constructor parameter or web action with the [FromKeyedServices] attribute, like this:
app.MapGet("/foo", ([FromKeyedServices("foo")] MyService myService) => myService.Whatever(123));
app.MapGet("/bar", ([FromKeyedServices("bar")] MyService myService) => myService.Whatever(123));From now on, when registering a named cache, we can simply add AsKeyedServiceByCacheName() like this:
services.AddFusionCache("MyCache")
.AsKeyedServiceByCacheName();and later we'll be able to have the named cache both as usual:
app.MapGet("/foo", (IFusionCacheProvider cacheProvider) => {
var cache = cacheProvider.GetCache("MyCache");
cache.Set("key", 123);
});and as a keyed service, like this:
app.MapGet("/foo", ([FromKeyedServices("MyCache")] IFusionCache cache) => {
cache.Set("key", 123);
});We can even use AsKeyedService(object? serviceKey) and specify a custom service key like for any other keyed service in .NET.
On top of being able to register FusionCache as a keyed service, we can even consume keyed services as FusionCache components, like memory cache, distributed cache, serializer, backplane, etc.
For more read at the official docs.
See here for the original issue.
⚡ Add PreferSyncSerialization option
It has been observed that in some situations async serialization and deserialization can be slower than the sync counterpart: this has nothing to do with FusionCache itself, but how serialization works in general.
So I added a new option called PreferSyncSerialization (default: false, fully backward compatible), that can allow the sync version to be preferred.
See here for the original issue.
🔭 Better OpenTelemetry traces for backplane notifications
Community user @imperugo noticed that when using the backplane with OpenTelemetry traces enabled, all the spans for the notifications incoming via the backplane were put under one single parent span, basically creating a single mega-span "containing" all the others.
Ideally, each span for each notification should be on their own, and now this is the case.
Also while I was at it I noticed another couple of things that, if added to the traces, could make the developer experience better.
In detail:
- include a tag with the source id (the InstanceId of the remote FusionCache instance)
- change the status of the trace in case of errors, like invalid notifications or similar
- add an event in case of, well, some event occurring during the activity
So yeah, I took this opportunity to make the overall experience better.
Finally, since backplane notifications can create a lot of background noise inside observability tools, I changed the default so that, even when there's a backplane setup, traces for backplane notifications are not enabled: to change this simply enable it at setup time.
See here for the original issue.
🐵 Add ChaosMemoryCache
Among all the chaos-related components already available, one to work with IMemoryCache was missing: not anymore.
✅ Better tests
Some more tests have been added, including better cross-platform snapshot tests.
📕 Docs
Updated some docs with the latest new things.
v1.2.0-preview1
🔑 Added DI Keyed Services support
Since .NET 8 we now have native support for multiple services of the same type, identified by different names, thanks to the addition of so called keyed services.
The idea is basically that we can now register services not only by type but also by specifying the name, like this:
services.AddKeyedSingleton<MyService>("foo");
services.AddKeyedSingleton<MyService>("bar");and later is possible to resolve it by both the type and a name.
Another way is to simply mark a constructor parameter or web action with the [FromKeyedServices] attribute, like this:
app.MapGet("/foo", ([FromKeyedServices("foo")] MyService myService) => myService.Whatever(123));
app.MapGet("/bar", ([FromKeyedServices("bar")] MyService myService) => myService.Whatever(123));From now on, when registering a named cache, we can simply add AsKeyedService() like this:
services.AddFusionCache("MyCache")
.AsKeyedService();and later we'll be able to have the named cache with something like this:
app.MapGet("/foo", ([FromKeyedServices("MyCache")] IFusionCache cache) => {
cache.Set("key", 123);
});Of course the named cache provider way is still available, like this:
app.MapGet("/foo", (IFusionCacheProvider cacheProvider) => {
var cache = cacheProvider.GetCache("foo");
cache.Set("key", 123);
});See here for the original issue.
⚡ Add PreferSyncSerialization option
It has been observed that in some situations async serialization and deserialization can be slower than the sync counterpart: this has nothing to do with FusionCache itself, but how serialization works in general.
So I added a new option called PreferSyncSerialization (default: false, fully backward compatible), that can allow the sync version to be preferred.
See here for the original issue.
🐵 Add ChaosMemoryCache
Among all the chaos-related components already available, one to work with IMemoryCache was missing: not anymore.
✅ Better tests
Some more tests have been added.
📕 Docs
Updated some docs with the latest new things.
v1.1.0
The theme for this release is some bug fixes, general quality of life improvements and some minor perf optimizations.
📞 Added a couple of missing OnMiss events
Community user @ConMur noticed that sometimes, in a couple of code paths related to distributed cache operations, FusionCache was missing some OnMiss events (no pun intended): now this has been fixed.
See here for the original issue.
💣 Better FailSafeMaxDuration handling
User @F2 and user @sabbadino both noticed that fail-safe max duration was not being respected all the times, particularly when multiple fail-safe activations actually occurred in sequence there was in fact the risk of extending the physical duration of the cache more than what should've been correct.
This has been fixed (while also introducing some nice memory and cpu savings!).
See here and here for the original issues.
💀 A rare case of deadlock
While doing some extensive testing community user @martindisch discovered a rare case of deadlock that was happening only when all of these conditions were met simultaneously:
- Eager Refresh enabled
- call
GetOrSet[Async]while passing aCancellationToken - the call that actually triggered the eager refresh is cancelled, after the eager refresh kicked in but before it finished
- not all the times, but only when the execution flow passed in a certain spot at a certain time
This issue kicked off an experimentation about a reworking of FusionCache internals regarding the general theme of cancellations of background factory executions in general (eager refresh, background factory completion with soft/hard timeouts, etc): I am happy to say that now the deadlock is gone for good.
To do that well I slightly changed the behaviour of FusionCache regarding background factory executions: now they cannot be cancelled anymore by cancelling the original request that generated them, since it doesn't make that much sense to begin with, since a cancellation is used to cancel the current operation, but a background execution (particularly with eager refresh) is basically a side effect, which does have a life of its own, so it doesn't make a lot of sense to cancel that, too.
All in all, there should be realistically no discernible externally observable difference in behaviour (and no more deadlocks!).
Finally, I've added some tests to detect these scenario to avoid future regressions.
See here for the original issue.
📢 Better AutoRecoveryDelay default value
The default value for AutoRecoveryDelay has been changed from 2s to 5s, to better align with the standard reconnect timing of StackExchange.Redis, which is the most commonly used implementation for the distributed cache and the backplane.
The idea is about "sensible defaults" and the overarching theme of "it just works": if the default distributed cache and backplane are Redis, let's just make sure that the defualt experience is better aligned with that (and also, when bad things happen in production, automatically recovering from it with a slightly longer delay is, pragmatically, really not a big deal).
🧽 Some code cleanup
Thanks to @SimonCropp the code has been cleaned up a little bit here, updated to the latest C# features there, plus some other minor tweaks. Thanks Simon!
🚀 Performance
In this release I've been able to squeeze in some minor but nice memory/cpu optimizations.
✅ Better tests
I added some more tests to have a higher code coverage.
📕 Docs
Updated some docs with the latest new things.
v1.0.0
FusionCache is now v1.0 🥳
Yes, it finally happened.
Let's see what this release includes.
🚀 Performance, performance everywhere
FusionCache always tried to be as optimized as possible, but sometimes useful new features took some precedence over micro-optimizing this or that.
Now that all the major features (and then some) are there, it was time to do a deep dive and optimize a cpu cycle here, remove an allocation there and tweak some hot path to achieve the best use of resources.
So here's a non-comprehensive list of nice performance improvements in this release:
- zero allocations/minimal cpu usage in Get happy path
- reduced allocations/cpu usage in Set happy path
- less allocations/cpu usage when not using distributed components
- less allocations/cpu usage (via closures) when using events
- zero allocations at all when not using logging (no support structures init for operationId generation)
- reduced overhead in some async code paths
Oh, and thanks to community member @neon-sunset for the issue highlighting some shortcomings, that now have been solved!
See here for the issue.
🦅 Better Eager Refresh (docs)
When executing an Eager Refresh, the initial check for an updated cache entry on the distributed cache is now totally non-blocking, for even better performance.
🆕 Added IgnoreIncomingBackplaneNotifications option (docs)
FusionCache always allowed to optionally skip sending backplane notifications granularly, for each operation (or globally thanks to DefaultEntryOptions): it was not possible though to ignore receiving them.
Now we may be thinking "why would I want to use a backplane, but not receive its notifications?" and the answer to that can be found in the feature request made by community member @celluj34 .
See here for the issue.
⚠️ Better nullability annotations for generic types
This is linked to the evolution of nullable reference types, nullables with generics and the related static analysis with each new version of c# and its compiler.
Along the years I tried to adjust the annotations to better handle generic types + nullables with each new version, because what the compiler allowed me to do and was able to infer changed at every release (the first version had problems with generics without where T : class/struct constraints, for example).
I've now updated them to reflect the latest behaviour, so that it's now more strict in the generic signatures, mostly for GetOrSet<T> and GetOrSetAsync<T>: in previous versions the return type was always nullable, so when calling GetOrSet<Person> we would have a return value of Person? (nullable) even if the call was not GetOrSet<Person?>.
Now this is better.
Thanks for community member @angularsen for highlighting this.
See here for the issue.
⚠️ Changed FusionCacheEntryOptions.Size to be nullable (docs)
The type of the Size option in the FusionCacheEntryOptions type has been historically long (default: 1): the underlying Size option in the MemoryCacheEntryOption type is instead long? (default: null).
So, to better align them, now the types and default values are the same.
🪞 Reflection no more
Not technically a problem per se, but with the release of the new and improved auto-recovery in v0.24.0, I had to add a little bit of reflection usage to support complex scenario of recovering some of the transient distributed errors.
Now, the small amount of code that was using reflection is gone, and this in turn means:
- overall better performance
- be better positioned for, eventually, playing with AOT (where reflection is basically a no-go)
See here for the issue.
🔭 Add eviction reason to Open Telemetry metrics
With v0.26.0 native support for Open Telemetry has been added to FusionCache.
Now community members @JoeShook noticed that the eviction reason was missing from the Eviction counter, which could be in fact useful.
Now it has been added, thanks Joe!
See here for the PR.
🔭 Removed cache instance id from Open Telemetry metrics
Community member @rafalzabrowarny noticed that FusionCache was adding a tag to the metrics, specifically one with the cache instance id: now, since it's a random value generated for every FusionCache instance, it will have a high cardinality and that is usually problematic with APM platforms and tools.
Now it's gone, thanks Rafał!
See here for the issue.
👷♂️ Better detection of incoherent CacheNames options
With the introduction of the builder in v0.20 FusionCache got a nice way to configure the various options and components, in a very flexible way.
In one particular scenario though, it was possible to specify something incoherent: a single instance with multiple CacheNames, specified in different ways by using both the high level AddFusionCache("MyCache") and the WithOptions(...) methods.
A couple of examples:
services.AddFusionCache("foo")
.WithOptions(options => {
options.CacheName = "bar";
});or, more subtly:
services.AddFusionCache()
.WithOptions(options => {
options.CacheName = "bar";
});Now FusionCache correctly detects this scenario and throws an exception as soon as possible, helping the developer by showing the golden path to follow and how to do to solve it.
Thanks @albx for spotting this!
See here for the issue.
👷♂️ Better builder auto-setup
Again with the builder, when using the TryWithAutoSetup() method in the builder it now also try to check for registered memory lockers by calling TryWithMemoryLocker(), automatically.
✅ Better tests
I added some more tests to have a higher code coverage, and made the snapshot tests better.
📜 Better logs
More detailed log messages in some areas where they could've been better (mostly related to the backplane).
📕 Docs
Updated some docs with the latest new things.
v1.0.0-preview2
Important
Yep, it's almost v1.0 time!
Please try this preview2 release and let me know if you find any issue, so the v1.0 can be as good as possible: from now until v1.0 is out I will no longer consider requests for new features.
Thanks 🙏
🚀 Performance, performance everywhere
FusionCache always tried to be as optimized as possible, but sometimes useful new features took some precedence over micro-optimizing this or that.
Now that all the major features (and then some) are there, it was time to do a deep dive and optimize a cpu cycle here, remove an allocation there and tweak some hot path to achieve the best use of resources.
So here's a non-comprehensive list of nice performance improvements in this release:
- zero allocations/minimal cpu usage in Get happy path
- minimal allocations/cpu usage in Set happy path
- less allocations/cpu usage when not using distributed components
- less allocations/cpu usage (via closures) when using events
- zero allocations at all when not using logging (no support structures init for operationId generation)
Oh, and thanks to community member @neon-sunset for the issue highlighting some shortcomings, that now have been solved!
See here for the issue.
🦅 Better Eager Refresh (docs)
When executing an Eager Refresh, the initial check for an updated cache entry on the distributed cache is now totally non-blocking, for even better performance.
🆕 Added IgnoreIncomingBackplaneNotifications option (docs)
FusionCache always allowed to optionally skip sending backplane notifications granularly, for each operation (or globally thanks to DefaultEntryOptions): it was not possible though to ignore receiving them.
Now we may be thinking "why would I want to use a backplane, but not receive its notifications?" and the answer to that can be found in the feature request made by community member @celluj34 .
See here for the issue.
⚠️ Better nullability annotations for generic types
This is linked to the evolution of nullable reference types, nullables with generics and the related static analysis with each new version of c# and its compiler.
Along the years I tried to adjust the annotations to better handle generic types + nullables with each new version, because what the compiler allowed me to do and was able to infer changed at every release (the first version had problems with generics without where T : class/struct constraints, for example).
I've now updated them to reflect the latest behaviour, so that it's now more strict in the generic signatures, mostly for GetOrSet<T> and GetOrSetAsync<T>: in previous versions the return type was always nullable, so when calling GetOrSet<Person> we would have a return value of Person? (nullable) even if the call was not GetOrSet<Person?>.
Now this is better.
Thanks for community member @angularsen for highlighting this.
See here for the issue.
⚠️ Changed FusionCacheEntryOptions.Size to be nullable (docs)
The type of the Size option in the FusionCacheEntryOptions type has been historically long (default: 1): the underlying Size option in the MemoryCacheEntryOption type is instead long? (default: null).
So, to better align them, now the types and default values are the same.
✅ Better tests
I added some more tests to have a higher code coverage, and made the snapshot tests better.
(Follows recap from preview1)
⚡ Reflection no more
Not technically a problem per se, but with the release of the new and improved auto-recovery in v0.24.0, I had to add a little bit of reflection usage to support complex scenario of recovering some of the transient distributed errors.
Now, the small amount of code that was using reflection is gone, and this in turn means:
- overall better performance
- be better positioned for, eventually, playing with AOT (where reflection is basically a no-go)
See here for the issue.
🔭 Add eviction reason to Open Telemetry metrics
With v0.26.0 native support for Open Telemetry has been added to FusionCache.
Now community members @JoeShook noticed that the eviction reason was missing from the Eviction counter, which could be in fact useful.
Now it has been added, thanks Joe!
See here for the PR.
🔭 Removed cache instance id from Open Telemetry metrics
Community member @rafalzabrowarny noticed that FusionCache was adding a tag to the metrics, specifically one with the cache instance id: now, since it's a random value generated for every FusionCache instance, it will have a high cardinality and that is usually problematic with APM platforms and tools.
Now it's gone, thanks Rafał!
See here for the issue.
👷♂️ Better detection of incoherent CacheNames options
With the introduction of the builder in v0.20 FusionCache got a nice way to configure the various options and components, in a very flexible way.
In one particular scenario though, it was possible to specify something incoherent: a single instance with multiple CacheNames, specified in different ways by using both the high level AddFusionCache("MyCache") and the WithOptions(...) methods.
A couple of examples:
services.AddFusionCache("foo")
.WithOptions(options => {
options.CacheName = "bar";
});or, more subtly:
services.AddFusionCache()
.WithOptions(options => {
options.CacheName = "bar";
});Now FusionCache correctly detects this scenario and throws an exception as soon as possible, helping the developer by showing the golden path to follow and how to do to solve it.
Thanks @albx for spotting this!
See here for the issue.
👷♂️ Better builder auto-setup
Again with the builder, when using the TryWithAutoSetup() method in the builder it now also try to check for registered memory lockers by calling TryWithMemoryLocker(), automatically.
📜 Better logs
More detailed log messages in some areas where they could've been better (mostly related to the backplane).
📕 Docs
Updated some docs with the latest new things.
v1.0.0-preview1
Important
Yep, it's almost v1.0 time!
Please try this preview1 release and let me know if you find any issue, so the v1.0 can be as good as possible: from now until v1.0 is out I will no longer consider requests for new features.
Thanks 🙏
⚡ Reflection no more
Not technically a problem per se, but with the release of the new and improved auto-recovery in v0.24.0, I had to add a little bit of reflection usage to support complex scenario of recovering some of the transient distributed errors.
Now, the small amount of code that was using reflection is gone, and this in turn means:
- overall better performance
- be better positioned for, eventually, playing with AOT (where reflection is basically a no-go)
See here for the issue.
🔭 Add eviction reason to Open Telemetry metrics
With v0.26.0 native support for Open Telemetry has been added to FusionCache.
Now community members @JoeShook noticed that the eviction reason was missing from the Eviction counter, which could be in fact useful.
Now it has been added, thanks Joe!
See here for the PR.
🔭 Removed cache instance id from Open Telemetry metrics
Community member @rafalzabrowarny noticed that FusionCache was adding a tag to the metrics, specifically one with the cache instance id: now, since it's a random value generated for every FusionCache instance, it will have a high cardinality and that is usually problematic with APM platforms and tools.
Now it's gone, thanks Rafał!
See here for the issue.
👷♂️ Better detection of incoherent CacheNames options
With the introduction of the builder in v0.20 FusionCache got a nice way to configure the various options and components, in a very flexible way.
In one particular scenario though, it was possible to specify something incoherent: a single instance with multiple CacheNames, specified in different ways by using both the high level AddFusionCache("MyCache") and the WithOptions(...) methods.
A couple of examples:
services.AddFusionCache("foo")
.WithOptions(options => {
options.CacheName = "bar";
});or, more subtly:
services.AddFusionCache()
.WithOptions(options => {
options.CacheName = "bar";
});Now FusionCache correctly detects this scenario and throws an exception as soon as possible, helping the developer by showing the golden path to follow and how to do to solve it.
Thanks @albx for spotting this!
See here for the issue.
👷♂️ Better builder auto-setup
Again with the builder, when using the TryWithAutoSetup() method in the builder it now also try to check for registered memory lockers by calling TryWithMemoryLocker(), automatically.
📜 Better logs
More detailed log messages in some areas where they could've been better (mostly related to the backplane).
📕 Docs
Updated some docs with the latest new things.
v0.26.0
Important
This version supersede v0.25.0 (now deprecated) because of a small breaking change: although it technically is a breaking change, it is about the new IFusionCacheMemoryLocker introduced just a week ago, so unless you are already implementing your own custom memory locker it will not be a problem.
Apart from this, v0.26.0 is basically the same as v0.25.0, so please update to v0.26.0 as soon as possible so you'll be ready for the big v1.0 that will be released very soon.
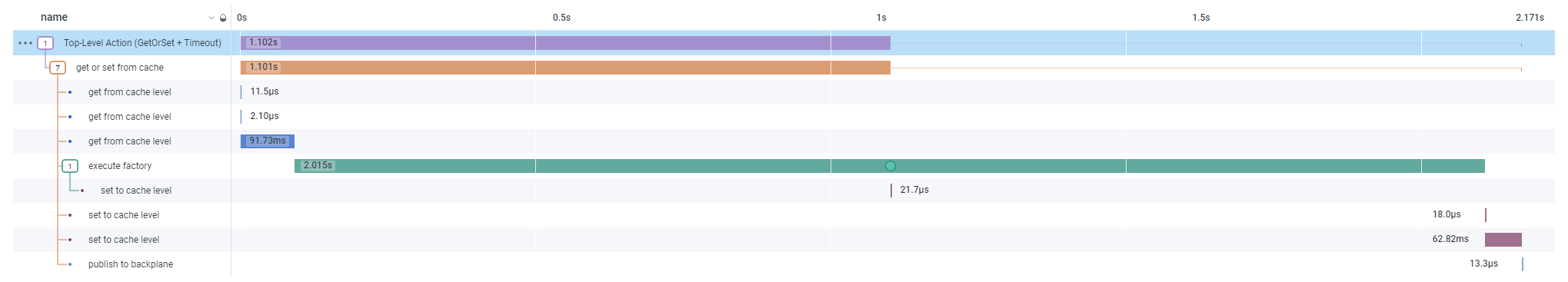
🔭 OpenTelemetry support (docs)
FusionCache now natively supports full observability, thanks to the great native support of OpenTelemetry in .NET via the core Activity and Meter classes without any extra dependency to produce them.
In general, the 3 main signals in the observability world are traces, metrics and logs.
FusionCache always supported logging, and even in a pretty advanced and customizable way.
Now the two remaining pieces are finally here: traces and metrics.
It is possible to opt-in to generate traces and metrics for both:
- high-level operations: things like
GetOrSet/Set/Removeoperations,Hit/Missevents, etc - low-level operations: things like memory/distributed level operations, backplane events, etc
There's also a new package specific for OpenTelemetry that adds native support to instrument our applications, with FusionCache specific options ready to use, like including low-level signals or not.
It is then possible to simply plug one of the existing OpenTelemetry-compatible collectors for systems like Jaeger, Prometheus or Honeycomb and voilà, there we have full observability of our FusionCache instances.
Here's an example of how to set it up without dependency injection:
// SETUP TRACES
using var tracerProvider = Sdk.CreateTracerProviderBuilder()
.AddFusionCacheInstrumentation()
.AddConsoleExporter()
.Build();
// SETUP METRICS
using var meterProvider = Sdk.CreateMeterProviderBuilder()
.AddFusionCacheInstrumentation()
.AddConsoleExporter()
.Build();or, via dependency injection:
services.AddOpenTelemetry()
// SETUP TRACES
.WithTracing(tracing => tracing
.AddFusionCacheInstrumentation()
.AddConsoleExporter()
)
// SETUP METRICS
.WithMetrics(metrics => metrics
.AddFusionCacheInstrumentation()
.AddConsoleExporter()
);The end result of all of this, when viewed for example in Honeycomb, is something like this:
Quite nice, uh 😏 ?
Oh, and I can't thank @martinjt enough for the support!
See here for the issue.
🔒 Extensible Memory Locker
FusionCache always protected us from the Cache Stampede problem, but the internals of the memory locking mechanism have always been private.
Now no more, and thanks to the new IFusionCacheMemoryLocker interface the community may come up with different designs and implementations.
The builder has also been extended with support for configuring different memory lockers thanks to new methods like WithRegisteredMemoryLocker, WithMemoryLocker(locker), WithStandardMemoryLocker() and more.
See here for the issue.
NOTE: this version contains a small breaking change regarding the params in the methods of IFusionCacheMemoryLocker (swapped the position of key and operationId, to be 100% consistent with the rest of the codebase. As explained in the note at the top it is something that realistically will not change anything, but it's good to know.
🐞 Fixed a minor SkipDistributedCacheReadWhenStale bug
Thanks to community member @angularsen I fixed a small bug related to SkipDistributedCacheReadWhenStale not working as expected during get-only operations (TryGet, GetOrDefault).
See here for the issue.
↩️ Better items cleanup for auto-recovery
Minor, but still: FusionCache now better cleans up processed auto-recovery items.
📕 Docs
Updated some docs and added some new ones (Observability, etc).
v0.25.0 (⚠️ deprecated)
Important
This version has been superseded by v0.26.0 because of a small breaking change: although it technically is a breaking change, it is about the new IFusionCacheMemoryLocker introduced just a week ago, so unless you are already implementing your own custom memory locker it will not be a problem.
Apart from this, v0.26.0 is basically the same as v0.25.0, so please update to v0.26.0 as soon as possible so you'll be ready for the big v1.0 that will be released very soon.
🔭 OpenTelemetry support (docs)
FusionCache now natively supports full observability, thanks to the great native support of OpenTelemetry in .NET via the core Activity and Meter classes without any extra dependency to produce them.
In general, the 3 main signals in the observability world are traces, metrics and logs.
FusionCache always supported logging, and even in a pretty advanced and customizable way.
Now the two remaining pieces are finally here: traces and metrics.
It is possible to opt-in to generate traces and metrics for both:
- high-level operations: things like
GetOrSet/Set/Removeoperations,Hit/Missevents, etc - low-level operations: things like memory/distributed level operations, backplane events, etc
There's also a new package specific for OpenTelemetry that adds native support to instrument our applications, with FusionCache specific options ready to use, like including low-level signals or not.
It is then possible to simply plug one of the existing OpenTelemetry-compatible collectors for systems like Jaeger, Prometheus or Honeycomb and voilà, there we have full observability of our FusionCache instances.
Here's an example of how to set it up without dependency injection:
// SETUP TRACES
using var tracerProvider = Sdk.CreateTracerProviderBuilder()
.AddFusionCacheInstrumentation()
.AddConsoleExporter()
.Build();
// SETUP METRICS
using var meterProvider = Sdk.CreateMeterProviderBuilder()
.AddFusionCacheInstrumentation()
.AddConsoleExporter()
.Build();or, via dependency injection:
services.AddOpenTelemetry()
// SETUP TRACES
.WithTracing(tracing => tracing
.AddFusionCacheInstrumentation()
.AddConsoleExporter()
)
// SETUP METRICS
.WithMetrics(metrics => metrics
.AddFusionCacheInstrumentation()
.AddConsoleExporter()
);The end result of all of this, when viewed for example in Honeycomb, is something like this:
Quite nice, uh 😏 ?
Oh, and I can't thank @martinjt enough for the support!
See here for the issue.
🔒 Extensible Memory Locker
FusionCache always protected us from the Cache Stampede problem, but the internals of the memory locking mechanism have always been private.
Now no more, and thanks to the new IFusionCacheMemoryLocker interface the community may come up with different designs and implementations.
The builder has also been extended with support for configuring different memory lockers thanks to new methods like WithRegisteredMemoryLocker, WithMemoryLocker(locker), WithStandardMemoryLocker() and more.
See here for the issue.
🐞 Fixed a minor SkipDistributedCacheReadWhenStale bug
Thanks to community member @angularsen I fixed a small bug related to SkipDistributedCacheReadWhenStale not working as expected during get-only operations (TryGet, GetOrDefault).
See here for the issue.
↩️ Better items cleanup for auto-recovery
Minor, but still: FusionCache now better cleans up processed auto-recovery items.
📕 Docs
Updated some docs and added some new ones (Observability, etc).